From Data
to Decision®
The Right Data for your Decisions, When and Where you Need it

Automate Your Decisions
Click, drag and drop your way to improved efficiency. Reduce human effort and increase speed for any process at your organization.
Learn More About Zoot's Instant Decisioning Solution
Put Data to Work
Enjoy one of the most robust portfolios of data connections available. Take advantage of more than 70 connected brands and hundreds of products to inform your decisions.
View Our Data Providers

Forget About Infrastructure
Operate in the purpose-built Zoot private cloud without having to operate and manage your own data centers. Enjoy the most secure, reliable, live environment for your decision and data requirements.
Zoot Opens Data Center in Australia
Grow With Confidence
When your business scales, you need partners who can keep up. Zoot will be there with you, proven by more than three decades of reliability, supporting some of the largest organizations in the world.
Global Payment Provider Case Study

“Zoot helped us think through what our solution would look like not just in the short term, but also the long term. We control it, we manage it, we build within it, the base structure is there. And if at any point we need support or help, it’s just a matter of getting on the phone.”
Global Head of Credit Risk and Operations, North America
Zoot’s Clients
BANKING
5 OF THE LARGEST US BANKS
E-COMMERCE
2 of the top global e-commerce sites
CREDIT CARD
4 OF THE TOP CREDIT CARD ISSUERS
MERCHANT
2 OF THE TOP MERCHANT ACQUIRERS
RETAIL
3 OF THE TOP US RETAILERS
HEALTHCARE
WELLNESS, PHARMACY AND INSURERS
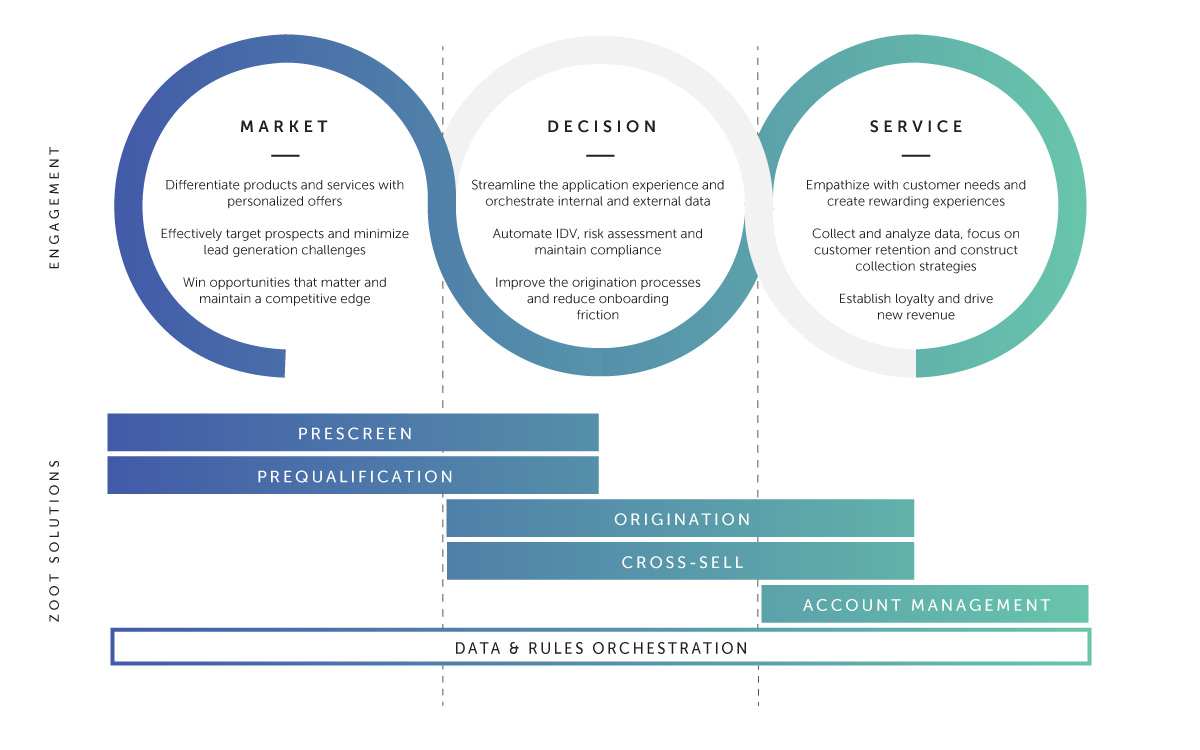
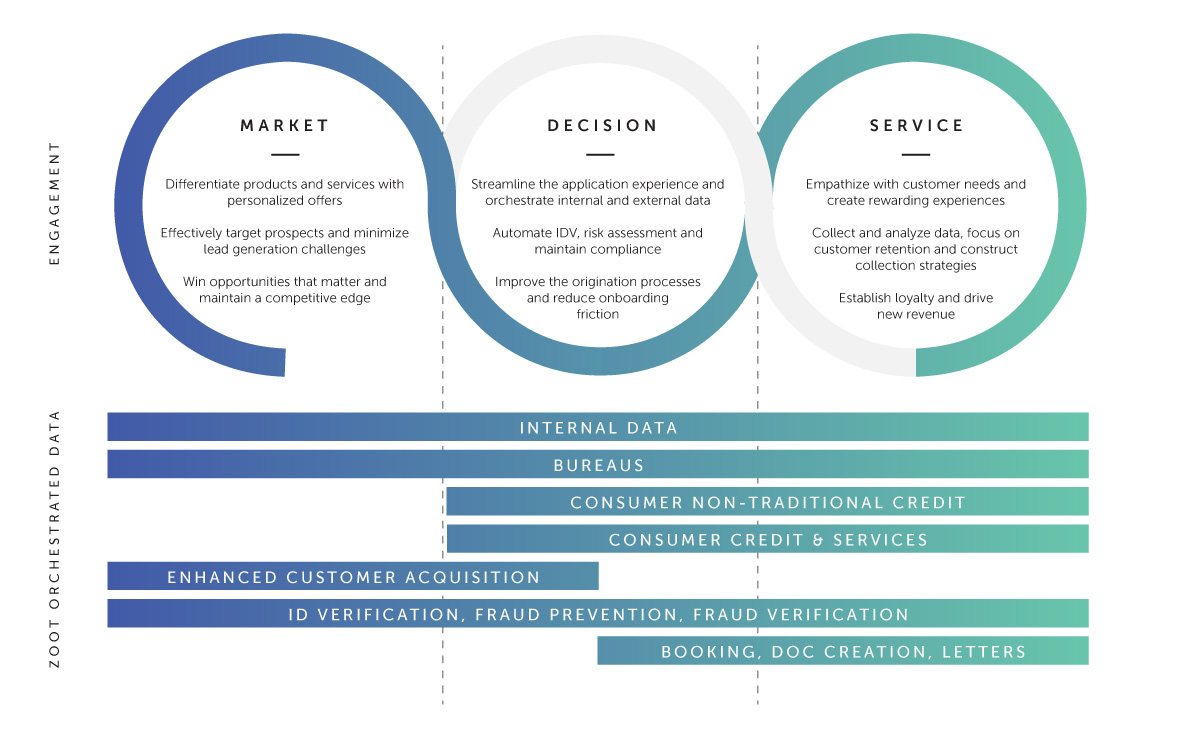
Supporting The Entire Customer Lifecycle
Zoot offers advanced capabilities and solutions to banks, financial institutions, and retailers. With Zoot, you can orchestrate data and business rules to target ideal customers, streamline decision-making processes, and access the right data at the right time to best service your customers.
Our solutions help clients improve customer engagement, increase efficiency, and reduce operational costs, making Zoot a valuable partner for organizations looking to enhance their customer lifecycle.
From The Library
CBA Live 2024: Key Takeaways
At the end of March, hundreds of bankers and industry leaders flocked to Washington, D.C. to discover key insights and network at CBA Live 2024,...
AI/ML Integration with Zoot
Infusing Artificial Intelligence into Decision Making. Keep Bad Actors at Bay. Infusing Artificial Intelligence into Decision MakingAI/ML...
Embrace Open Banking [Exciting New 2024 Updates]
Open banking can still be a bit controversial. Banks, fintechs, and other financial institutions (FIs) have typically had what you...